 Toshiba’s Cambridge Research Lab has demonstrated 200Gbit/s quantum cryptography – quantum key protected data transmission – over a single 100km long cable, which is a world record.
Toshiba’s Cambridge Research Lab has demonstrated 200Gbit/s quantum cryptography – quantum key protected data transmission – over a single 100km long cable, which is a world record.
It used six wavelength channels in total, two each at 100Gbit/s for the data and four including data and clock channels for the quantum keys.
One of the things that makes the scheme difficult is cross-talk: the conventionally encoded data bits are each represented by over a million photons, while bits in the quantum key are received on a single photon. Raman scattering spills data photons into the key channel.
“Lots of scattered light makes detecting key photons difficult,” Dr Andrew Shields, assistant MD of Toshiba Research Europe, told Electronics Weekly. “We filter the arriving key channel light in wavelength and time.”
Wavelength filtering is through a optical bandpass filter – narrower than those used in normal WDM (wavelength division multiplexed) fibre networks, and time filtering is based opening the receiver only when a key photon might be expected – a key photon is sent every nanosecond, signalled by the clock channel, and is around ~100ps long at the receiver.
Single photons
The key is encoded onto the phase of single photons. “We could encode polarisation, but we chose to use phase,” said Shields.
Detecting the phase of single photons at high speed is tricky to say the least.
For this 1Gphoton/s receivers has been developed that uses semiconductor-based avalanche photodiodes on each of two output ports of an interferometer – one for each expected phase state.
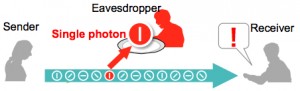
In quantum cryptography, the key is sent in a snoop-proof manner – according to the known laws of physics.
To send the key, pulses of photons are modulated with a key bit. Then, before they are launched into the fibre, they are heavily attenuated to have less than one photon per pulse on average – so some pulses have been completely absorbed.
Once in the fibre, remaining photons, which are still phase-modulated, either make it to the far end or is scattered away en-route.
Sender and receiver exchange information about which photons actually arrived, but not about the their states – ‘the first photon, the tenth photon, the……’, for example.
In this way, both ends know which photons arrived, and what their phase encoding was, but a snooper can only watch the back-channel and learn which photons arrived, not their phase.
Schrödinger’s cat
If the snooper tries to measure the phase as the photons pass, the phase will be corrupted – It is a Schrödinger’s cat situation, said Shields: “A man in the middle will change the encoding. There is nothing they can do to gain knowledge without changing the state of the encoded photons. They will always reveal themselves.”
Being able to send whole keys in less than 1ms means the key can be changed at more than 1kHz, cutting the length of data stream encoded with a single key, therefore further reducing the chance that statistical analysis will reverse-engineer the key from the encrypted data. For a fibre length of 36km, the secure key rate exceeds 1.9Mbit/s, sufficient for over 5,000 encryption keys per second.
For the record-breaking trial, which broke the Lab’s own 40Gbit/s record, Toshiba’s Cambridge Research Lab worked with ADVA Optical Networking (which provided the data transmission system) and BT’s R&D hub at Adastral Park near Ipswich where the demonstration took place.
Secure the genome
Toshiba is also involved in a system to secure genome data using quantum cryptography in Sendai, Japan.
This kind of data is unique in that it might have to stay secure for many human generations. “If it is encrypted using today’s technology, someone might save it [snooped data] and decrypt it when computers are more powerful,” said Shields. “You can’t do this with quantum encrypted data, even with quantum computers.”
Governments and banks are other potential users.
The next step in Cambridge is to build a network and demonstrate end-to-end quantum cryptography through that. According to Shields, his team has already demonstrated it working through an optical switch. “If the network is all-optical, we are able to form quantum keys end-to-end,” he said. “If it has electrical switching, the intermediate nodes have to be placed in a physically-secure area, for example at a telco or company office. There are ways to the possibility of attack against intermediate nodes: using secret sharing schemes, for example.”
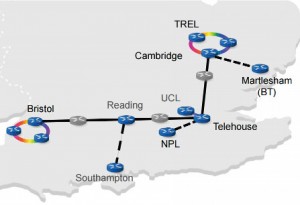 The Cambridge team is also collaborating in an EPSRC-funded long-term trial involving building a Cambridge-London-Bristol quantum cryptography network with metro networks at the Cambridge and Bristol nodes. Potential users will be able to use it for application development.
The Cambridge team is also collaborating in an EPSRC-funded long-term trial involving building a Cambridge-London-Bristol quantum cryptography network with metro networks at the Cambridge and Bristol nodes. Potential users will be able to use it for application development.
steve bush



![b-robotaxi-a-20151002[1]](http://static.electronicsweekly.com/news/wp-content/uploads/sites/16/2015/10/b-robotaxi-a-201510021-300x225.jpg)